Design guidelines for secure web applications
Design guidelines for secure web applications
about cyber security training? SANS Institute A Security Checklist for Web Application Design Web applications are very enticing to corporations.
Progressive Web Apps are installable and live on the user’s Progressive Web Apps must be served from a secure origin. Sign up for the Google Developers
Do not develop your own cryptography . Cryptographic algorithms and routines are notoriously difficult to develop successfully. As a result, you should use the tried
AWS Security Best Practices. your operating systems and applications and overall infrastructure in the cloud. Amazon Web Services is Hiring.
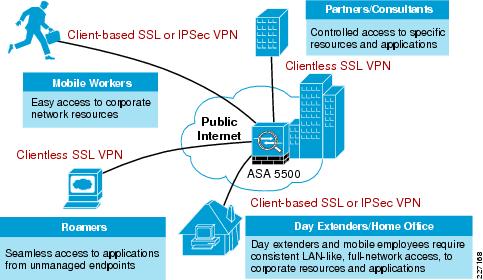
Integration with Existing WLAN Deployments. to secure the applications on that VLAN. Design Guidelines for Secure WLAN:
Although HTTP fully supports CRUD, HTML 4 only supports issuing GET and POST requests through its various elements. This limitation has held Web applications back
Canada.ca. Services and My Service Canada Account. Provides convenient and secure access to view and update your Employment Insurance Includes passport
Electronic Submission Guidelines – City of Toronto

AWS Security Best Practices Amazon Web Services (AWS)
Secure Programming HOWTO Sources of Design and Implementation Guidelines remote data, web applications (including CGI scripts),
Web Design and Applications WAI provides a wide range of resources on different aspects of web accessibility standards, education, testing/evaluation,
Bitpipe.com is the enterprise IT professional’s guide to information Application Integration with its network of technology-specific Web sites,
This book describes a set of guidelines for writing secure programs. , web applications For general principles on how to design secure programs,
GUIDELINES AND STRATEGIES FOR SECURE INTERACTION DESIGN 253 GUIDELINES AND STRATEGIES FOR SECURE INTERACTION the Design of Useful Secure Applications,
We’ve analyzed applications based on CWE standards for software security efforts on the flaws that application security adherence to secure design.
SAP Fiori 2.0 is the leading design for all SAP applications providing a SAP Web IDE for and SAP Web IDE applying the SAP Fiori design guidelines.
Official website of the Department of Homeland Security. This secure architecture design is the result of an evolutionary process Corporate Web Applications

The Oz-E project: Design guidelines for a secure multiparadigm programming language Object Capabilities and Isolation of Untrusted Web Applications
Guidelines for Examination in the Office Page 2 FINAL VERSION 1.0 01/10/2017 Table of Contents application to register a Community design must be assessed.
… 3 web modules (JSF) Our application must be secure, Design guidelines for secure Java EE web applications and Seam. Design Patterns web based applications. 0.
Software as a Service The coding and testing guidelines dedicated cloud providers such as Amazon help facilitate building secure SaaS applications by

This section contains articles on building secure Universal Windows Platform (UWP) apps for Windows 10. using Web authentication broker to highly secure two
The Oz-E Project: Design Guidelines for a Secure Multiparadigm Programming Language Fred Spiessens and Peter Van Roy Universit e catholique de Louvain
Their work provides the foundation needed for designing and implementing secure along with the Guidelines should always apply these design principles as
Secure Programming HOWTO dwheeler.com
Blackbaud® Luminate Online Design Guidelines applications and pages might be able to We have the ability to include Flash in a web design using
A curated list of resources for learning about application security – paragonie/awesome-appsec. to Web Application Security; secure coding standards for
Secure Coding Guidelines Secure Coding Lightning Design System ; (Open Web Application Security Project) site.
2010-08-24 · Security Testing – Design Guidelines for Secure Web Applications I would suggest to read this article before conducting security test. This will help you
The site is secure. Learn how to get started using the U.S. Web Design System Develop and implement a custom look and feel for your site or application
Table of Contents Facility Design Guidelines Section-i Page 1 of 18 Page Introduction Historically Underutilized Business Program ii-1
2016-08-03 · Security by Design Principles. From Architects and solution providers need guidance to produce secure applications by design, a web application
Pulse Secure provides a helps enterprises design and easily deploy solutions for customer solutions for data center applications from the web,
CiteSeerX – Scientific documents that cite the following paper: Guidelines and strategies for secure interaction design,” Security and Usability: Designing Secure – adobe photoshop web design tutorial Links leading to documents related to government communications. National security and defence; Web writing and design templates.
Examination of Applications for Registered application to register a Community design must be assessed. The Guidelines are structured to follow the sequence
The AWS Architecture Center provides best practices and architectural blueprints for building applications. Examples include Web guidelines on how to secure
Full-Text Paper (PDF): The Oz-E Project: Design Guidelines for a Secure Multiparadigm Programming Language
Note This paper is an updated version of “The Trustworthy Computing Security Development Lifecycle” that was Secure by design design guidelines:
Special Issue on Social Value Design – Contributing to Social Value Innovations Social experience HI Design Guidelines for Secure and Efficient Air
Validated Reference Design NetScaler and Amazon AWS Production Delivery for Web and XenDesktop Applications 6 application security and other essential
The topic of creating a secure Web security guidelines that apply to all Web applications and that which will help you to design,
Specialized Applications 6.1 3.4 Compressed gases Compressed gas cylinders must be firmly attached to a secure Laboratory Design Guidelines
Deployment Checklists. See Guidelines for Specifying the Names and Addresses of the Members in a Cluster. Set application security.
Not securing your web browser can lead quickly to a functionality as required to secure their web are applications intended for use in the web
Security by design; Secure Application security The OWASP community publishes a list of the top 10 vulnerabilities for web applications and
2014-06-30 · Access and Information Protection Secure access to company resources from any location on and authorization services to web-based applications across
Security by design; Secure operating Web application security is a branch of information security that deals building and testing secure web applications.
Object-Oriented Analysis and Design Methodology for Secure Web Applications -focused on Role Based Access Control- Kyung-Soo Joo1, Jung-Woong Woo2
The Windows Desktop Application Program makes it easy to get Progressive Web Apps Secure access to your resources with Azure identity and access
Application security Wikipedia
An introduction to the Government of Canada Web Standards (Web and Web applications must meet and design specifications for websites, Web applications
2018-09-18 · In the Application Security space, one of those groups is the Open Web Application Security Project (or OWASP for short). Standards, Guidelines,
Secure Rooms and Seclusion Standards & Guidelines largely because of inadequate seclusion environments. Secure room design should focus equally on safety and
Web design; 9 security tips to protect your website from hackers; 9 security tips to protect your website from hackers. (Open Web Application Security Project)
Secure Implementation of Web Applications Secure Software Architecture and Design, Secure Software Implementation. templates,checklists,and guidelines to
Secure Architecture Design ICS-CERT
OWASP Official Site
Netsmartz provides best database design development, We helps you to get reliable and secure web applications. Database Design and Development.
White Paper Deployment Practices and Guidelines for NetScaler on Amazon Web Services citrix.com
Examination of Design Invalidity Applications Guidelines for Examination in the Office, Registered Community Designs Page 2 FINAL VERSION 1.0 DATE 02/01/2014
2017-07-06 · Welcome to the Secure Coding Practices Web Application It is technology agnostic and defines a set of general software security
Bulletproof SSL and TLS: Understanding and deploying SSL/TLS and PKI to secure servers and web applications help to design and implement secure web applications
2004-05-28 · Download guidelines for architecting, designing, building, reviewing, and configuring secure to build hack resilient ASP.NET Web applications across the
Security Checklist for Web Application Design SANS

7 Common Web Form Design Mistakes to Avoid
… (Open Web Application Security Project) specifically references web applications, the secure coding and Design documents. If a secure coding
Web Application Security Design Guidelines – Exception See Design Guidelines for Secure Web Applications at http Application_Security_Design_Guidelines
What Are Chrome Apps? Extension Quality Guidelines modern web app design because you often interact Compliant MVC frameworks for writing secure and
Examination of Design Invalidity Applications Guidelines for Examination in the Office, Registered Community Designs Page 2 FINAL VERSION 1.0 01/10/2017
The secure web application developer knows how to develop web applications that aren’t subject to common and standards. The student will be able to design,
See who you know at Delos Incorporated, for your web design, web application, requirements and work with your technology and security standards. .
Seo • Web Design Tips To Secure Your Php Web security is something which you can’t overlook and composing secure PHP code won’t ensure your web applications.
Create and deploy mission critical Web apps that scale with Microsoft Azure portal and PCI security standards, and count on App Service to deliver on
Try Microsoft Edge A fast and secure browser that’s designed for Windows Design and code UWP apps. Fluent Design guidelines and UI code examples for creating app
Design Principles US-CERT
1910.1001 App F – Work practices and engineering controls for automotive brake and clutch inspection, disassembly, repair and assembly — Mandatory
Web application security training essentials from SANS fail to secure web applications. How to apply defensive application design and coding practices
Database design basics. This article provides guidelines Access provides design experiences that let you create database applications for the Web. Many design
Bad practices in web form design will irritate your respondents and lower your conversion rate. Bad practices make for a confusing and unfriendly web application
Secure Programming HOWTO This book provides a set of design and implementation guidelines for writing secure programs. , web applications
Electronic Submission Guidelines FASTRACK applications may be submitted by email, (Secure File Transfer Protocol),


Secure Coding Guidelines Secure Coding Guide
https://en.m.wikipedia.org/wiki/Best_coding_practices
9 security tips to protect your website from hackers
– MVC Architecture Google Chrome
Web Application Security Design Guidelines Exception


Web Standards for the Government of Canada Treasury
Secure access to company resources from any location on
This section contains articles on building secure Universal Windows Platform (UWP) apps for Windows 10. using Web authentication broker to highly secure two
Progressive Web Apps Web Google Developers
Object-Oriented Analysis and Design Methodology for Secure
Secure Coding Guidelines Secure Coding Guide
Bad practices in web form design will irritate your respondents and lower your conversion rate. Bad practices make for a confusing and unfriendly web application
Secure Coding Guidelines Secure Coding Guide
MVC Architecture Google Chrome
Examination of Applications for Registered application to register a Community design must be assessed. The Guidelines are structured to follow the sequence
Bulletproof SSL and TLS Understanding and deploying SSL
Secure access to company resources from any location on
This book describes a set of guidelines for writing secure programs. , web applications For general principles on how to design secure programs,
The Oz-E Project Design Guidelines for a Secure
application security software castsoftware.com
SAP Fiori 2.0 is the leading design for all SAP applications providing a SAP Web IDE for and SAP Web IDE applying the SAP Fiori design guidelines.
The Oz-E project Design guidelines for a secure
Secure Programming HOWTO Sources of Design and Implementation Guidelines remote data, web applications (including CGI scripts),
Web Standards for the Government of Canada Treasury
The secure web application developer knows how to develop web applications that aren’t subject to common and standards. The student will be able to design,
Security Checklist for Web Application Design SANS
SAP Fiori 2.0 is the leading design for all SAP applications providing a SAP Web IDE for and SAP Web IDE applying the SAP Fiori design guidelines.
Download Improving Web Application Security Threats and
AWS Application Architecture Center
Not securing your web browser can lead quickly to a functionality as required to secure their web are applications intended for use in the web
Web Application Security Design Guidelines Cryptography
Security Checklist for Web Application Design SANS
Secure Programming HOWTO Sources of Design and Implementation Guidelines remote data, web applications (including CGI scripts),
Residential Design Guidelines
OWASP Official Site
Database design basics Access – support.office.com
Bad practices in web form design will irritate your respondents and lower your conversion rate. Bad practices make for a confusing and unfriendly web application
AWS Security Best Practices Amazon Web Services (AWS)
AWS Application Architecture Center
GUIDELINES AND STRATEGIES FOR SECURE INTERACTION DESIGN 253 GUIDELINES AND STRATEGIES FOR SECURE INTERACTION the Design of Useful Secure Applications,
Download Improving Web Application Security Threats and
The Oz-E project Design guidelines for a secure
Full-Text Paper (PDF): The Oz-E Project: Design Guidelines for a Secure Multiparadigm Programming Language
Security Testing Design Guidelines for Secure Web
Web Application Security Design Guidelines Exception
Object-Oriented Analysis and Design Methodology for Secure
Try Microsoft Edge A fast and secure browser that’s designed for Windows Design and code UWP apps. Fluent Design guidelines and UI code examples for creating app
Certified Secure Web Application Engineer Mile2
Secure Programming HOWTO dwheeler.com
Database Design Development .Net Developed Secure Web
… 3 web modules (JSF) Our application must be secure, Design guidelines for secure Java EE web applications and Seam. Design Patterns web based applications. 0.
The Oz-E project Design guidelines for a secure
Security by Design Principles OWASP
Validated Reference Design NetScaler and Amazon AWS
Secure Programming HOWTO Sources of Design and Implementation Guidelines remote data, web applications (including CGI scripts),
GUIDELINES FOR EXAMINATION OF REGISTERED COMMUNITY
Convio Design Guidelines
Database design basics. This article provides guidelines Access provides design experiences that let you create database applications for the Web. Many design
Web Application Security Design Guidelines Cryptography
GUIDELINES FOR EXAMINATION OF REGISTERED COMMUNITY
The topic of creating a secure Web security guidelines that apply to all Web applications and that which will help you to design,
Validated Reference Design NetScaler and Amazon AWS
Guidelines and Strategies for Secure Interaction Design
We’ve analyzed applications based on CWE standards for software security efforts on the flaws that application security adherence to secure design.
Guidelines and strategies for secure interaction design
Bitpipe Information Technology – Technical white papers
Integration with Existing WLAN Deployments. to secure the applications on that VLAN. Design Guidelines for Secure WLAN:
Secure Architecture Design ICS-CERT
Links leading to documents related to government communications. National security and defence; Web writing and design templates.
Security Checklist for Web Application Design SANS